Programs/Applications Used
- Kali Linux
- Ghidra
straceltrace
Useful Links
- https://stackoverflow.com/questions/18410344/program-received-signal-sigill-illegal-instruction
- https://cplusplus.com/reference/cstring/strncmp/
- https://cplusplus.com/reference/cstring/strlen/
- https://osandamalith.com/2019/02/11/linux-reverse-engineering-ctfs-for-beginners/
Preliminary Steps
The first step to begin with is reading challenge description and checking the downloads. We have a binary file, so can start by just trying to run it.
Binary Analysis
Upon trying to run the file, we simply get another prompt.
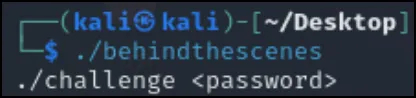
So now to use strace and ltrace to see what they give:
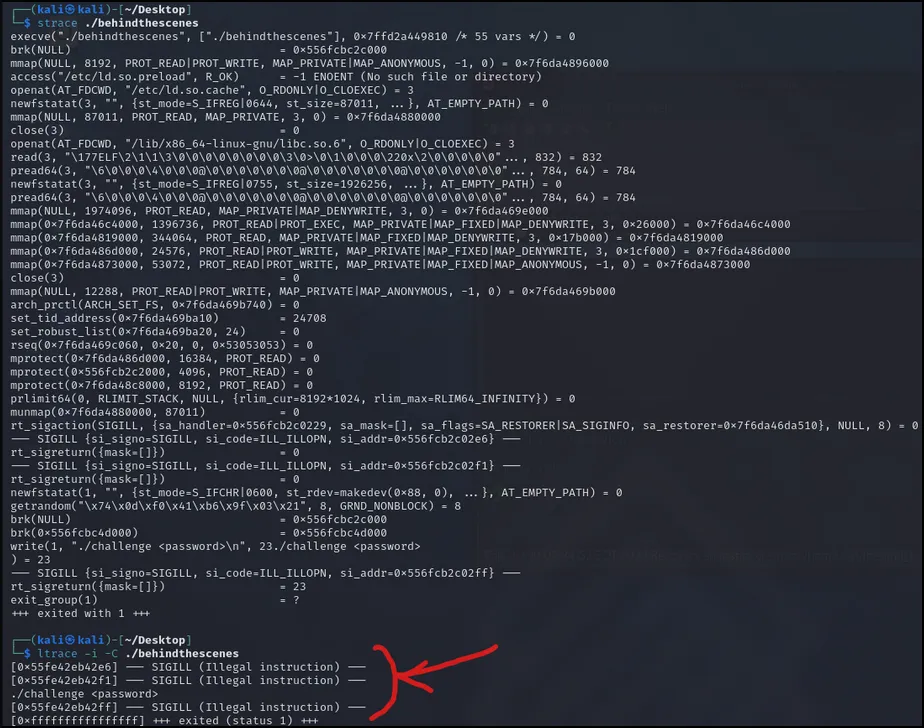
Seeing this SIGILL, I looked up what that means (see above) and then opened up the executable in Ghidra and headed to the main().
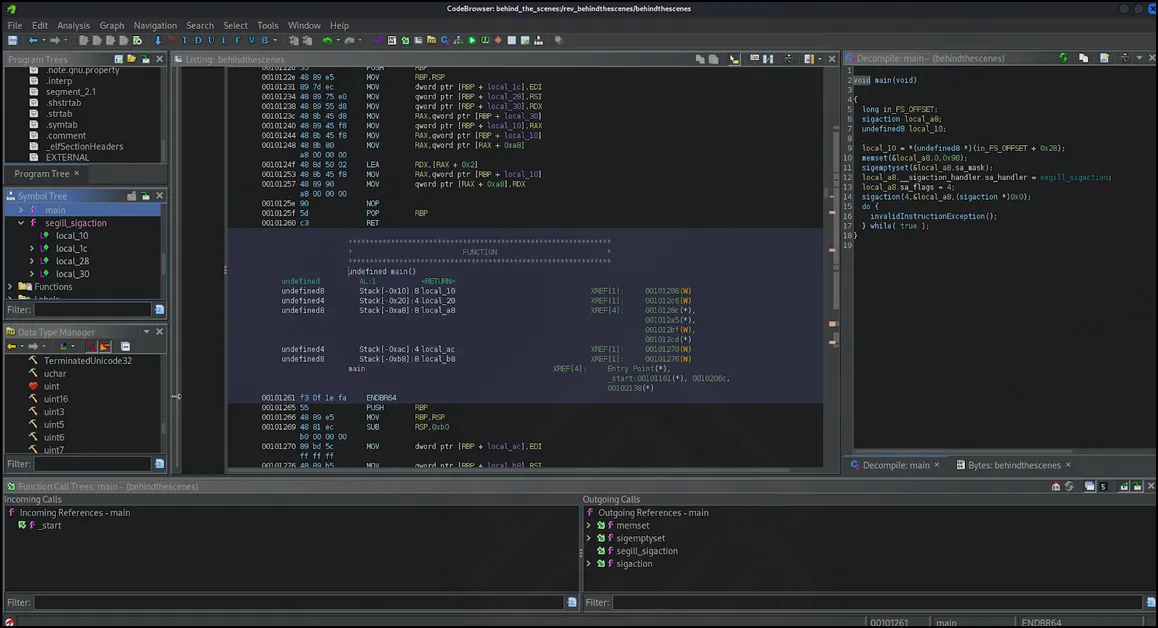
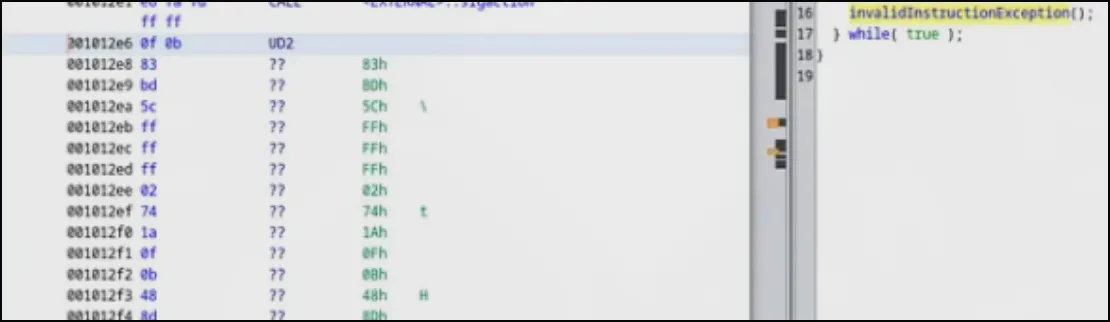
Here I saw the UD2 mentioned in the stackoverflow post, so began to decompile each one (Right click, decompile):
At this point, while decompiling each one, I noticed the strlen function, and then noticed the strncmp external call as well below this. I noticed that in the first strncmp function it had the plain text ‘Itz’ at the end of the variable as well:
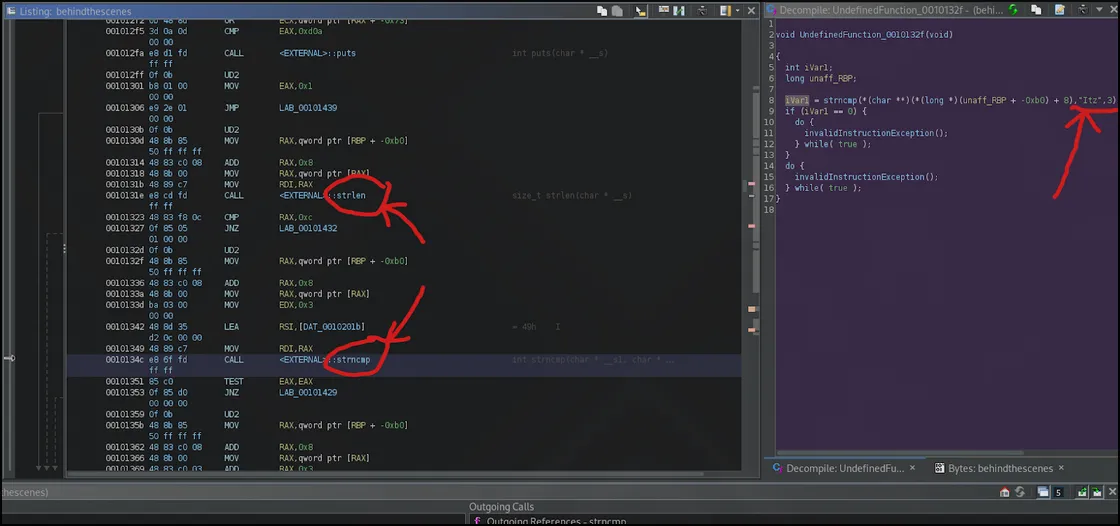
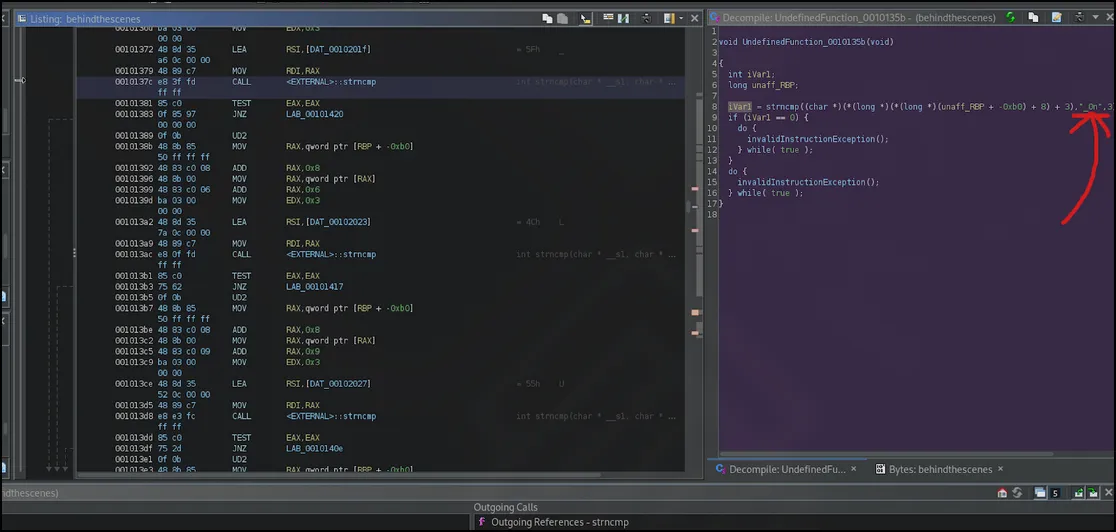
Going down each strncmp, I also found the print that states what format the flag would be printed in:
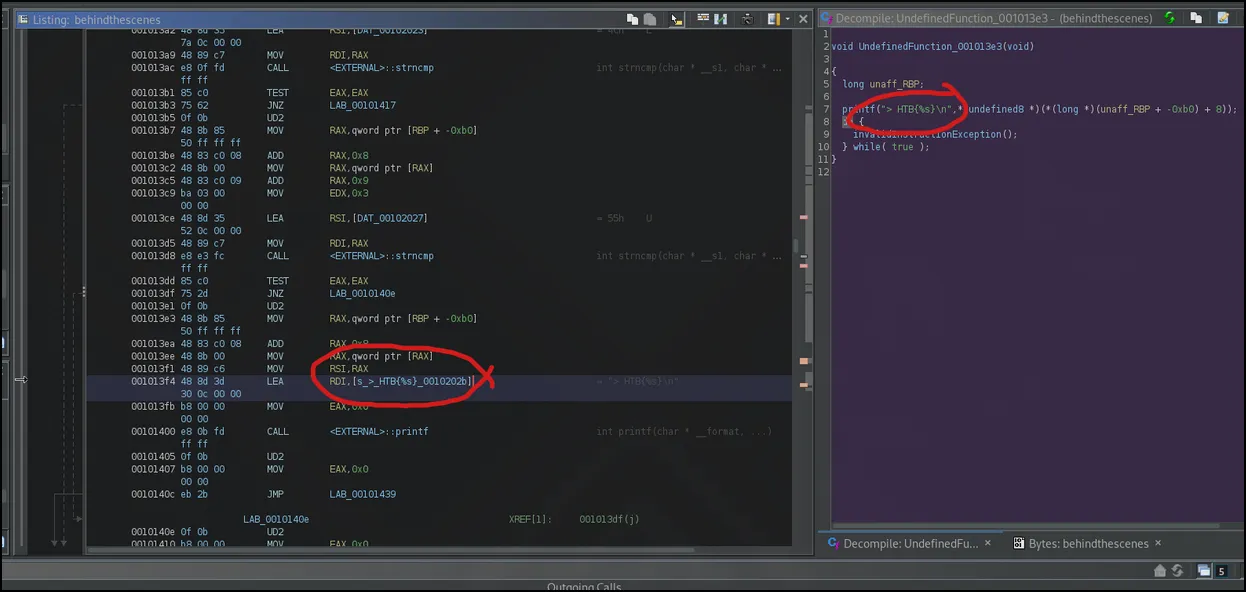
After doing this, the flag came out to be:
HTB{Itz_0nLy_UD2}
Powered by Fuwari